Overview
Time, Technology and Trade, these three things moves today’s world. All things depend on these things. Technology splits our times smaller. So people can calculate his expenditure in every split time. But as a nation we are falling behind in every sector as we are not utilizing these things properly.
At present situation, we collect Bangladesh Railway information manually. It’s a lengthy and complex process especially in the vacations. People suffer very much at this situation and they don’t have enough information of all railways. The queue is bigger in the national holidays and in the occasions. On the other hand Bangladesh Railway don’t have any online base information system by which they can come closer and give more flexible service to their clients.
We developed this web portal (www.bris.com) to reduce people suffering and avoid the complex manual collecting information system of the Bangladesh Railway.
Objectives of this Project
Our objective is to use the technology in such a way that a business can go fast and also consume time. It’s a total automation system for traveling companies particularly “Bangladesh Railway”.
The main points are –
- Get all the service information of the Bangladesh Railways.
- Maintaining a central data base.
- Easy to maintain.
- A more organized system for Bangladesh Railway than the manual.
- Insure a quality support for the general people.
- Anyone can see the seat plan (In graphical mode) from the web.
- Reduce suffering of the travelers.
Methodology
A software development methodology refers to the framework that is used to structure, plan, and control the process of developing an information system. A wide variety of such frameworks have evolved over the years, each with its own recognized strengths and weaknesses. One system development methodology is not necessarily suitable for use by all projects. Each of the available methodologies is best suited to specific kinds of projects, based on various technical, organizational, project and team considerations.
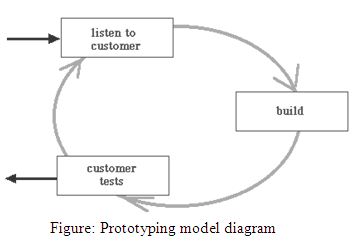
To develop and maintain this kind of web project, I choose ‘Prototyping Model’ as software development life cycle (SDLC). I think that to comply with the changing requirements and functionality, Prototyping Mode will be suitable comparing to other SDLC models.
Prototyping Model
Prototyping is the framework of activities during software development of creating prototypes, i.e., incomplete versions of the software program being developed.
- Full system requirements are not always available at the outset of a project.
- Customer is unsure of just what functionalities should be provided.
- Developer may be unsure of the “best” solution
- Human –computer interaction issues
- The prototyping model is designed for these situations
Advantages of prototyping
There are many advantages to using prototyping in software development – some tangible, some abstract.
- Reduced time and costs: Prototyping can improve the quality of requirements and specifications provided to developers. Because changes cost exponentially more to implement as they are detected later in development, the early determination of what the user really wants can result in faster and less expensive software.
- Improved and increased user involvement: Prototyping requires user involvement and allows them to see and interact with a prototype allowing them to provide better and more complete feedback and specifications
Reason for choosing Prototyping Model
It has been found that prototyping is very effective in the analysis and design of on-line systems, especially for transaction processing, where the use of screen dialogs is much more in evidence. The greater the interaction between the computer and the user, the greater the benefit is that can be obtained from building a quick system and letting the user play with it. Systems with little user interaction, such as batch processing or systems that mostly do calculations benefit little from prototyping. Sometimes, the coding needed to perform the system functions may be too intensive and the potential gains that prototyping could provide are too small. Prototyping is especially good for designing good human-computer interfaces.
So considering the above comparisons, it is clear that prototyping model is more appropriate and suitable for this consultation web project.
SWOT Analysis
SWOT analysis is an important factor of Railway Information System. It involves to some important. SWOT analysis is also necessary for our project.
SWOT analysis questions might be like
Strength:
• What does the system do well?
• Is our system strong in its market?
Weaknesses:
• How does the system do properly?
• What problems could be avoided?
Opportunities:
• Are IT industry threads moving upward?
• Are there new technologies that the company can exploit?
Threats:
• What are competitors doing well?
Result of SWOT analysis might be like
Strength:
• Information directly to the general people.
• Minimize cost and time.
Weaknesses:
• No strong relationships with Railway authority.
Opportunities:
• General people get information directly from this portal. .
Organization of the Project
This project is divided into some different parts like Introduction, System Analysis and Design, Implementation and Testing, Conclusion, Scope for future work, Appendix, References.
Tools
- PHP
- HTML
- CSS
- Java Script
- Mysql
- Wamp Server
- Adobe Photoshop
- Dreamweaver
System Analysis & Design
Requirement Analysis
A flawless method of requirement analysis is to determine the requirements or needs for
meeting the quality of the product. We carry out the entire system of requirement capture or
analysis, in specific ways. This starts with Requirement Gathering phase through which, we
elicit the necessary requirements of the people. We investigate scope and definite the new
system. Through the fact finding methods, we collect valid information from the potential
users. It helps in understanding the resistance offered by the misunderstanding and unrealistic
exceptions continuing in the current system. This is done through different mentioned ways.
Then comes the need for Requirement Determination, We implement this necessary step to
analyze the importance and substance of the chalked out requirements and check whether they
are ambiguous, incomplete and contradictory. Later we resolve these issues in a downright
professional manner, to bring out the real necessity and essence of the stated requirements.
For all new system the requirement analysis process should maintain a feasibility study.
Analysis of Feasibility
1. Technical feasibility:
Technical feasibility depends on hardware and software. The feasibility study will need to consider whether the level of technological advancement for the purpose has yet been reached and to determine the availability and the stability of the appropriate technology. It will need to establish that the proposed approach would be likely to process the require volume of transaction and give require times.
2. Operational feasibility:
Operational feasibility depends on the human, institutional and political aspect. The issues to be considered are the effect of the proposed changes on people’s job. The study must assess the change will be workforce.
3. Economic feasibility
Current system’s cost and benefits analysis.
Proposed system cost and benefits analysis.
Compare the both system.
4. Behavioral feasibility
People are inherently resistant to change, and computers have been known to change to facilitate change. An estimate should be made of how strong a reaction the user staff is likely to have toward the development of a computerized system. It is common knowledge that computer installations have something to do with turnover. Transfer, training and changes in employee job status. Therefore, it is under stable that the introduction of a candidate system requires special effort to educate, sell and train the staff on new ways of conducting business.
Objectives of feasibility study
Feasibility study is a short, focused study which aims to answer number of questions.
- Does the system contribute to the overall objectives of the organizations?
- Can the system be implemented using current technology and within give cost and schedule constraints?
- Can the system be integrated with other systems which are already in place?
The advantage of proposed system:
- Friendly and easy to use interface.
- Good storage.
- Well organized information system
- Very easy to official work.
- Cost effectiveness.
- Extensive lookup and search feature.
- Secure.
- Very much efficient.
After analyze the whole requirement, we have created web portal Bangladesh Railway Information System.it is completely computerized and online base system. It is a website usually maintained with Train schedule and fare information. People can get their required destination Train schedule on home by through the internet. In manual system, it is very time consuming, inefficient and complex. Our Online portal provides information for Train with fare & stoppage, so the people can easily get information as well as save their times.
Our designed web portal is totally free of cost, information base web portal. We developed this portal for fulfilling main two purposes. One is reduce general people suffering and get the opportunity to search all Bangladesh Railways information. And another is beginning the online base information system.
Website Design
Good design can make good quality website. Website design sits at the technical kernel of the software engineering process. Once project requirements have been analyzed and specified then website design will require three technical activities: design, code generation and testing.
The importance of website design can be started with a single word- “quality”. Design is the place where quality is the fostered in website development. Design provides us with representation of website that can be assessed for quality design, the way that can accurately translates a customer’s requirements into a finished product or system. Without design, we risk making unstable system that will fail small changes that can be made. Without design the system may be difficult to test.
The process and the stages
Website design is an iterative process through which requirements are translated into a “blueprint” for contrasting the software initially the blueprint depicts a holistic vies of website. The design is represented at a high level of abstraction that can be directly to a specific data, functional and behavioral requirements. The process and the stage of system design are logical and physical.
System design goes through logical and physical design with emphasis on the following:
- Preparing I/O specification.
- Preparing security and control specification and specifying the implementation plan.
- Preparing a logical design walkthrough before implementation.
Structured Design
Structured design is a data flow based methodology that identifies I/O and describes the functional aspects of the system. It partitions the program into a hierarchy of module organized in a top down manner with the details of the bottom. Structured Analysis views a system from the perspective of the data flowing through it. The function of the system is described by processes that transform the data flows. Structured analysis takes advantage of information hiding through successive decomposition (or top down) analysis. This allows attention to be focused on pertinent details and avoids confusion from looking at irrelevant details. As the level of detail increases, the breadth of information is reduced. The result of structured analysis is a set of related graphical diagrams, process descriptions, and data definitions. They describe the transformations that need to take place and the data required to meet a system’s functional requirement.
Output
Standard for printed output suggest giving each output a name or title providing a sample of the output layer and specifying the procedure for providing the accuracy of the output data. The output devices to conceder deepened on the capability of the devices with the system, response time requirements, and the printed quality required.
List of Outputs
- Train Name: Specify the all train name and train code number
- Train Category: Bangladesh Railway has many categories train service likes 1. Intercity 2. Mail Train 3. Local Train.
- From – To: Train starting point to destination Point
- Start Time: Train starting time from the desire station
- Sub Station: List of all substations and their list.
- Fare: Ticket Fare for your journey
- Off Day: Bangladesh Railway Train Service has an Off Day for train maintenance purpose. Here I include the Off Day information.
Output List Design
Output Table for Train Service
|
IntercityDhaka – Dewangong Bazar07:30 AMClick HereClick HereMonday
Dewangong Bazar – Dhaka02:10 PMMonday Jamuna express
IntercityDhaka – Tarakandi04:40 PMClick HereClick HereNo Tarakandi – Dhaka02:30 AM No Bhramanputra express
IntercityDhaka – Dewangong Bazar06:00 PMClick HereClick HereNo Dewangong Bazar – Dhaka06;00 AM No
Inputs
User Inputs of the Projects
- From
- To
Details of User Inputs
- From: Staring station of journey
- To: Destination station of journey.
Admin Inputs
- Train Name
- Train Category
- From – To
- Start Time
- Sub Station
- Sub Station Name
- Up Time
- Down Time
- Fare (Taka)
- Fare (Taka)
- Train Name
- From
- To
- AC (bath)
- AC (Seat)
- 1st Class Seat
- Snigdha
- Shuvon Chair
- Shuvon
- Shulov
- Off Day
Database Design
Database
The world of websites believes on creativities and extra ordinary works. Website owners always try to get user attention towards their website by accepting different type of tools and applications for their website. Whatever the information we get from the website it is done by the database, without database we cannot store our information and can’t show our data to others. So, it is very important to develop database web application development properly for modern website.
Different application which we use in our daily life like; online shopping, corporate website, news or games related websites etc. If you have a website which offer users online shopping and your database hasn’t been designed well then you should stop dreaming about money instantly. Thus proper designing of website must need. Web application Development always makes the things easier to get perfect result and it is referred as a software process in which a software process in which a software product is developed in proper way.
Database Management Concept
A database is a structured collection of data. The data are typically organized to model relevant aspects of reality (for example, the availability of rooms in hotels), in a way that supports processes requiring this information (for example, finding a hotel with vacancies).
The term database is correctly applied to the data and their supporting data structures, and not to the database management system (DBMS). The database data collection with DBMS is called a database system.
The term database system implies that the data are managed to some level of quality (measured in terms of accuracy, availability, usability, and resilience) and this in turn often implies the use of a general-purpose database management system (DBMS). A general-purpose DBMS is typically a complex software system that meets many usage requirements to properly maintain its databases which are often large and complex.
This is specially the case with client-server, near-real time transactional systems, in which multiple users have access to data; data is concurrently entered and inquired for in ways that preclude single-thread batch processing. Most of the complexity of those requirements is still present with personal, desktop-based database systems.
Well known DBMSs include Oracle, FoxPro, IBM DB2, Linter, Microsoft Access, Microsoft SQL Server, MY SQL, Post greSQL and SQLite. A database is not generally portable across different DBMS, but different DBMSs can inter-operate to some degree by using standards like SQL and ODBC together to support a single application built over more than one database. A DBMS also needs to provide effective run-time execution to properly support.
A way to classify databases involves the type of their contents, for example: bibliographic, document-text, statistical, or multimedia objects. Another way is by their application area, for example: accounting, music compositions, movies, banking, manufacturing, or insurance.
The term database may be narrowed to specify particular aspects of organized collection of data and may refer to the logical database, to the physical database as data content in computer data storage or to many other database sub-definitions.
General purposes of database system
A DBMS has evolved into a complex software system and its development typically requires thousands of person-years of development effort. Some general-purpose DBMSs, like Oracle, Microsoft SQL Server, FoxPro, and IBM DB2, have been undergoing upgrades for thirty years or more. General-purpose DBMSs aim to satisfy as many applications as possible, which typically makes them even more complex than special-purpose databases. However, the fact that they can be used “off the shelf”, as well as their amortized cost over many applications and instances, makes them an attractive alternative (Vs. one-time development) whenever they meet an application’s requirements.
Though attractive in many cases, a general-purpose DBMS is not always the optimal solution: When certain applications are pervasive with many operating instances, each with many users, a general-purpose DBMS may introduce unnecessary overhead and too large “footprint” (too large amount of unnecessary, unutilized software code). Such applications usually justify dedicated development. Typical examples are email systems, though they need to possess certain DBMS properties: email systems are built in a way that optimizes email messages handling and managing, and do not need significant portions of a general-purpose DBMS functionality.
Primary key and foreign key
The primary key of a relational table uniquely identifies each record in the table. It can either be a normal attribute that is guaranteed to be unique (such as Social Security Number in a table with no more than one record per person) or it can be generated by the DBMS (such as a globally unique identifier, or GUID, in Microsoft SQL Server). Primary keys may consist of a single attribute or multiple attributes in combination.
A foreign key is a field in a relational table that matches a candidate key of another table. The foreign key can be used to cross-reference tables.
Table Design
We are Create Five Tables for our Website.
- User Tab
- Train Tab
- Station Tab
- Travel Tab
- Stoppage Tap
Description of the Field of Tables
Table : User Tab
| Field Name | Type |
| User ID | integer |
| User Name | varcharacter |
| Password | Text |
Table: Train Tab
| Field Name | Type |
| Train ID | Integer |
| Train Name | Varcharacter |
| Category | Varcharacter |
| Details | Varcharacter |
| Up Time | integer |
| Down Time | Varcharacter |
| Start Place | Varcharacter |
| End Place | Varcharacter |
| Off Day | Varcharacter |
Table: Station Tab
| Field Name | Type |
| ID | Integer |
| Name | Varcharacter |
| City | Varcharacter |
| District | Varcharacter |
Table: Travel Tab
| Field Name | Type |
| ID | Integer |
| Train ID | Double |
| Station From | Text |
| Station To | Text |
| Cabin | Text |
| AC | Text |
| First Class | Text |
| Chair | Text |
| Shovon | Text |
| Shulov | Text |
| Other | Text |
Table: Stoppage Tab
| Field Name | Type |
| ID | Varcharacter |
| Station Id | Varcharacter |
| Up Time | Varcharacter |
| Down Time | Varcharacter |
Data Modeling
Data modeling is the process of designing and validating a database. Logical and physical data models contain terms and symbols to identify and represent all of the data objects needed for a business operation to function.
According to Hoberman (2009), “A data model is a way finding tool for both business and IT professionals, which uses a set of symbols and text to precisely explain a subset of real information to improve communication within the organization and thereby lead to a more flexible and stable application environment.”
Entity Relationship Diagram
The relationship (E-R) data model is based on a perception of a real world that consists of a collection of basic objects called entities and relationship. The relationship is an association among several entities.
There are three basic notations that an E-R data model implies:
- Entity Sets: The entity set is a set of Entities of the same type which are unique.
- Relationship Set: A relationship is an association among several entities.
- Attribute: The properties of an attributes are known as attribute.
An E-R diagram can express the overall logical structure of a database graphically. The E-R diagram of Online Sales Management System:
Use Case Diagram
One of the objectives of the system analysis process is to generate a collection of use cases. Use case describes the user’s view of the system. It helps to understand clearly what users want. Actors are typically outside the system, whereas use cases are inside.
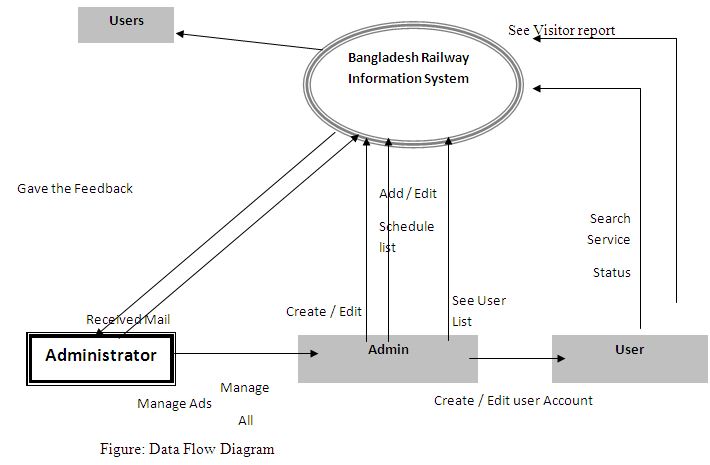
Data Flow Diagram
Data flow Diagram was first developed by Larry Constantine as a way of expressing system requirements in a graphical form; this led to module design.
A DFD also known as a “bubble chart” has the purpose of clarifying system requirement and identifying major transformations that will become programs in system design.
Web Security
Site Security
Security is one of the foremost concerns of every site administrator – and if it isn’t, it should be. Placing our site on the public Internet is an open invitation to intruders of every sort, and we need to be able to handle them, no matter how small or specialized your site may be. Fortunately, PHP can help to protect a site and users’ data. One can also use PHP’s built-in functions to make his own authentication system. Here discuss the more common types of attacks a site may encounter.
Cookie
A cookie, also known as a tracking cookie, browser cookie, and HTTP cookie, is a text file stored as plain text on a user’s computer by a web browser. A cookie consist of one or more name value pairs containing bits of information, which may be encrypted for information privacy and data security purposes.
The cookie is sent as an HTTP header by a web server to a web browser and then sent back unchanged by the browser each time it accesses that server. A cookie can be used for authentication, session tracking (state maintenance), storing site preferences, shopping cart contains, the identifier for a server-based session, or anything else that can be accomplished through storing textual data.
As text, cookies are not executable. Because they are not executed, they cannot replicate themselves and are not viruses. Due to the browser mechanism to set and read cookies, they can be used as spyware. Anti-spyware products may warn users about some cookies because cookies can be used to track people or violate privacy concerns.
Uses
Session management
Cookies may be used to maintain data related to the user during navigation, possibly across multiple visits. Cookies were introduced to provide a way to implement a “shopping cart” (or “shopping basket”), a virtual device into which users can store items they want to purchase as they navigate throughout the site.
Shopping basket applications today usually store the list of basket contents in a database on the server side, rather than storing basket items in the cookie itself. A web server typically sends a cookie containing a unique session identifier. The web browser will send back that session identifier with each subsequent request and shopping basket items are stored associated with a unique session identifier.
Allowing users to log in to s website is a frequent use of cookies. Typically the web server will first send a cookie containing a unique session identifier. Users then submit their credential and the web application authenticates the session and allows the user access to services.
Personalization
Cookies may be used to remember the information about the user who has visited a website in order to show relevant content in the future. For example a web server may send a cookie containing the username last used to log in to a website so that it may be filled in for future visits.
Many website use cookies for personalization based on users’ preferences users select preference. Users select their preferences by entering them in a web form and submitting the form to server. The server encodes the preferences in a cookie and sends the cookie back to the browser. This way, every time the user accesses a page, the server is also sent the cookie where the preferences are stored, and can personalize the page according to user preferences. For example, the Wikipedia website allows authenticated users to choose the webpage skin they like best; Google search engine allows users (even non registered ones) to decide how many search results per page they want to see.
Tracking
Tracking cookies may be used to track internet users’ web browsing habits. This can also be done in part by using the IP address of the computer requesting the page or referrer field of the HTTP header, but cookies allow for a greater precision. This can be done for example as follows:
- If the user requests a page of the site, but the request contains no cookie, the server presumes that this is the first page visited by the user; the server creat a random string and sends it as a cookie back to the browser together with the requested page;
- From this point on, the cookie will be automatically sent by browser to the server every time a new page from the site is requested; the server sends the page as usual, but also stores the URL of the requested page, the date/time of the request, and the cookie in a log file.
Misconceptions
Since their introduction on the Internet, misconceptions about cookies have circulated on the Internet and in the media. In 1998, CIAC, a computer incident response team of the United States Department of Energy, found the security vulnerability “essentially nonexistent” and explained that “information about where you come from and what web pages you visit already exists in a web server’s log file”. In 2005, Jupiter Research published the results of a survey, according to which a consistent percentage of respondents believed some of the following false claims:
- Cookies are like viruses in that they can infect the user’s hard disks.
- Cookies generate pop-ups
- Cookies are used for spamming
- Cookies are used only for advertising
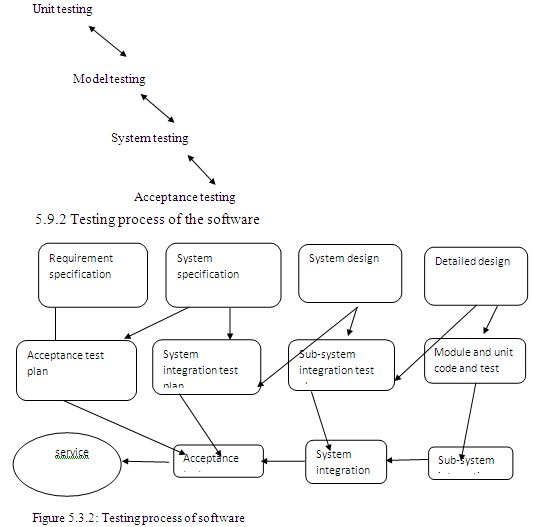
Testing
Software testing is a process used to help identify the correctness, completeness, security and quality of developed computer software. Software testing is an investigation conducted to provide stakeholders with information about the quality of the product or service under test. Software testing can also provide an objective, independent view of the software to allow the business to appreciate and understand the risks of software implementation. Test techniques include, but are not limited to, the process of executing a program or application with the intent of finding software bugs (errors or other defects).
Software testing can be stated as the process of validating and verifying that a computer program/application/product:
- meets the requirements that guided its design and development,
- works as expected,
- can be implemented with the same characteristics,
- And satisfies the needs of stakeholders.
Software testing, depending on the testing method employed, can be implemented at any time in the development process. Traditionally most of the test effort occurs after the requirements have been defined and the coding process has been completed, but in the agile approaches most of the test effort is on-going. As such, the methodology of the test is governed by the chosen software development methodology.
Different software development models will focus the test effort at different points in the development process. Newer development models, such as Agile, often employ test-driven development and place an increased portion of the testing in the hands of the developer, before it reaches a formal team of testers. In a more traditional model, most of the test execution occurs after the requirements have been defined and the coding process has been completed.
There are many approaches to software testing but effective testing of complex product is essentially a process of investigation, not merely a matter of creating and following routine procedure. Definition of testing is ‘’the process of questioning a product in order to evaluate it”, where the “questions” are operations the tester attempts execute with the product and the product answer with its behavior in reaction to the probing of the tester. A good test is sometimes described as one which revels an error; however, incomer recent thinking suggest that a good test is one which revels information of interest to someone who matters within the project community.
Testing Documentation
Different type of testing
- Unit testing.
- Integration testing.
- Validation testing.
- Output testing.
- User acceptances testing.
Unit testing
Unit Testing is a level of the software testing process where individual units/components of a software/system are tested. The purpose is to validate that each unit of the software performs as designed. A unit is the smallest testable part of software. It usually has one or a few inputs and usually a single output. In procedural programming a unit may be an individual program, function, procedure, etc. In object-oriented programming, the smallest unit is a method, which may belong to a base/super class, abstract class or derived/child class. (Some treat a module of an application as a unit. This is to be discouraged as there will probably be many individual units within that module.)
Unit testing frameworks, drivers, stubs and mock or fake objects are used to assist in unit testing.
Integration testing
Integration Testing is a level of the software testing process where individual units are combined and tested as a group. The purpose of this level of testing is to expose faults in the interaction between integrated units. Test drivers and test stubs are used to assist in Integration Testing .the objectives is to take unit tested modules and build a program
Structure that has been dictated by design. All modules are combined in this testing step. Then the program is tested as a whole and choose usually result.
Validation testing
The process of evaluating software during or at the end of the development process to determine whether it satisfies specified requirements. In other words, validation ensures that the product actually meets the user’s needs, and that the specifications were correct in the first place, while verification is ensuring that the product has been built according to the requirements and design specifications. Validation ensures that “you built the right thing”. Verification ensures that “you built it right”. Validation confirms that the product, as provided, will fulfill its intended use.
Output testing
After performing the validation testing, the next step are output testing of the proposed system could be useful if it is does not produce the required output in the specified format, the output generated or displayed by the system under consideration are tested by comparing with the format required by user. Here the output format is considered into two ways. One is on screen another is printed format. The output format on the screen is found to be correct as the format designed in the system design phase according to the user needs. For the hard copy also, the output comes out as specified required by the user. Hence output testing does not result any correction in the system.
User acceptance testing
User acceptance of system is the key factor for the success of any system. The system under consideration was tested for user acceptance by constantly keeping in touch with the prospective system users at the time developing and making changes wherever required.
System testing
During the system phase, the developing team validates the completely integrated system by testing end to end capabilities according to the system test plan. The system test plan is based on the requirements and specification document. Successfully completing the test specified in the test plan demonstrates that the system satisfies the requirements. In this phase, the developers correct any errors uncovered by system test. They also refine the draft user guide and produce an initial system description document. System testing is complete when all test specified in the system test plan have been run successfully.
Acceptance testing
In the acceptance testing phase, the system is tested by an independent acceptance test team to ensure that the software meets all requirements. Acceptance tests are created from user stories. During iteration the user stories selected during the iteration planning meeting will be translated into acceptance tests. The customer specifies scenarios to test when a user story has been correctly implemented. A story can have one or many acceptance tests, whatever it takes to ensure the functionality works.
Acceptance tests are black box system tests. Each acceptance test represents some expected result from the system. Customers are responsible for verifying the correctness of the acceptance tests and reviewing test scores to decide which failed tests are of highest priority. Acceptance tests are also used as regression tests prior to a production release.
Conclusion
We live in the age of modern science. Things are getting change by the use of technology .people are very concern about changing their life style. They do not want to waste their valuable time. Modern science is helpful to lead people’s life smoothly and firstly.
Now days, internet is one of the inventions of the modern technology. It is a system, providing us a million data, knowledge, picture etc. and so many features. Our project “online sales management system” is based on the internet.
Now we are live in the modern science and technology. So every work is controlled by computer. So bearing in mind all these things we have developed our site for working with various sections like any kind of train schedule information. It is an online information system so people can get data from anywhere by the use of online. In this site we have provided so many options for the people, like start to destination search option with category. We hope that this site will work properly for the peoples saving their times, cost etc. management of costs. Our main goal is to show a system to give the user a better experience for their getting information.
Scope of the further development
The Scope of the further works regarding the present work is:
- The site to be developed with more information
- The ticket reservation system will be added next time.
- The search engine will be work more quickly.
- It will be very user friendly.